Why Data Access Is the New Frontline of Cybersecurity
Access control is no longer optional—it's the foundation of secure, compliant, and scalable data systems. Learn why it's the missing layer in most organizations' security stacks.
Part 1: The Problem Space — Why Access Control is Often Overlooked
In many organizations, data security efforts are focused at the edges—firewalls, endpoint protection, encryption in transit. While these are critical layers of defense, they often overlook the simplest and most common vulnerability: internal overexposure to sensitive data.
Think about this: how many employees in your company have access to files they don’t really need? It could be:
A former intern who still has access to a shared finance folder
A junior developer able to read production environment secrets
A marketing contractor with full access to customer PII
These are not hypothetical situations—they happen constantly.
According to IBM’s 2023 Cost of a Data Breach Report, nearly 1 in 5 breaches are caused by insiders—many of them unintentional or due to excessive access privileges.
The issue? No access review policy. No clear data classification. No internal boundaries.
Without proper access control, you don’t just risk exposure—you lose visibility. When something goes wrong, you may not know:
Who accessed the data?
When did they download it?
Were they even supposed to see it?
Access control is not about restricting access—it’s about intentionally granting access to the right people, for the right reasons, with the right guardrails in place.
Part 2: Why Access Control Belongs in Your Security Stack
Access control isn’t a nice-to-have—it’s the foundation that ties together your data protection strategy. Without it, you can’t enforce policies, prove compliance, or build trust.
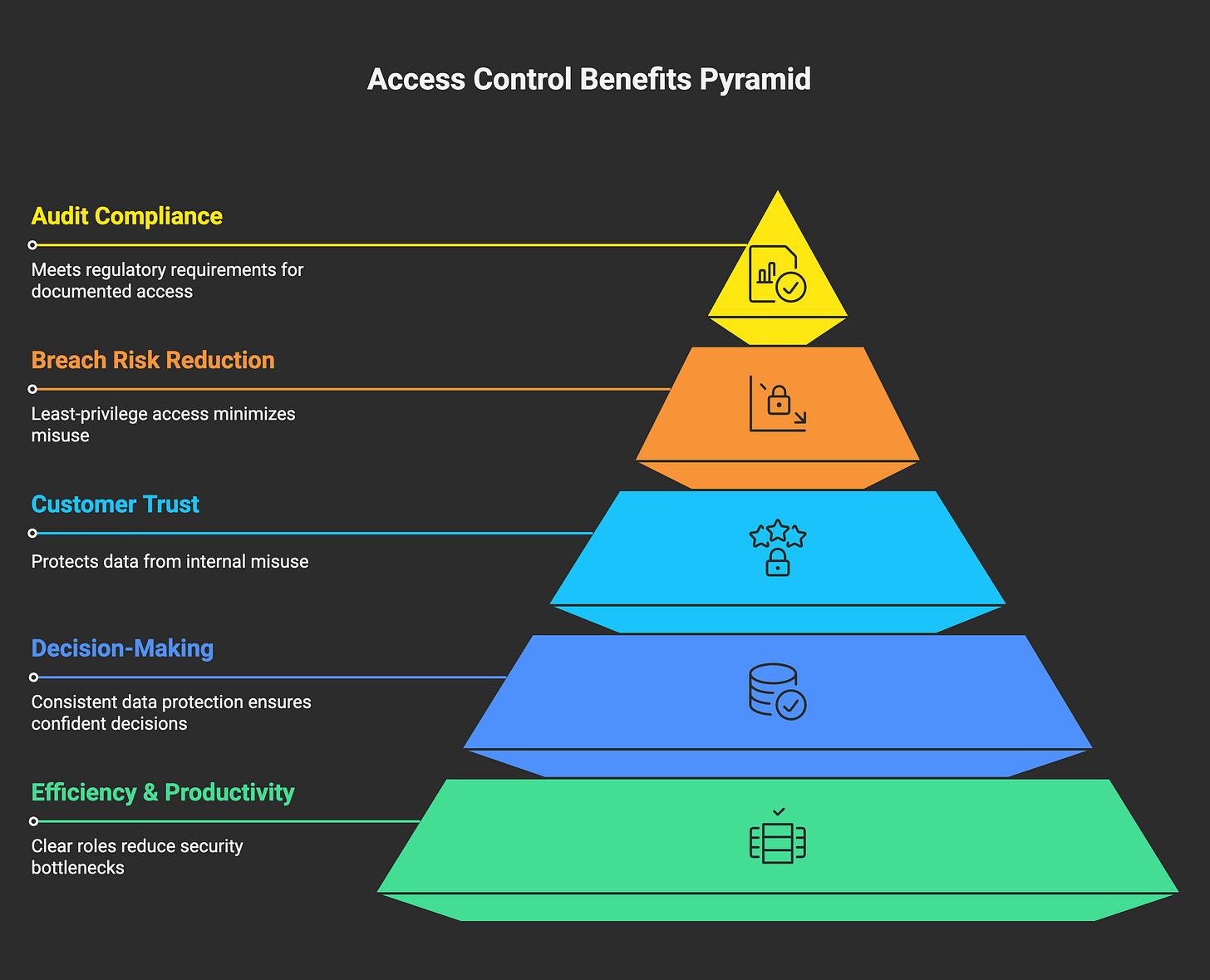
1. Increased Efficiency and Productivity
With clearly defined roles and permissions, teams get what they need—no ticket queues or security bottlenecks.
Example: A data analyst accesses pre-approved sales data directly in a governed workspace, without asking IT for credentials.
2. Improved Decision-Making
When data is consistently classified and protected, leaders can make fast, confident decisions with full traceability.
Example: Finance runs quarterly forecasts using verified, access-controlled data pipelines that log every change.
3. Enhanced Customer Trust
Customers expect their data to be protected—not just externally, but from misuse inside the company.
Example: A healthcare startup assures patients that only licensed clinicians can access their records, using access controls tied to credentials.
4. Lower Breach Risk
With least-privilege access, there's less chance that someone stumbles into something sensitive—or that their credentials are misused.
5. Audit-Ready Compliance
Frameworks like HIPAA, GDPR, SOC 2, and PCI-DSS all require controlled, documented access.
Part 3: Core Elements of Access Control in Data Governance
Access control isn’t just a policy—it’s a critical part of how data governance is implemented in the real world. While governance sets the rules, access control enforces them. Without strong enforcement mechanisms, even the most well-documented policies remain theoretical. Below are key elements that operationalize data access within a secure framework:
1. Data Classification
Before deciding who can access what, an organization needs to understand what kind of data it holds. Data classification involves labeling data by sensitivity and criticality—such as confidential, internal use, or public. This step lays the groundwork for access control because it dictates the level of protection each category requires.
For example, salary information or healthcare records should only be accessible to HR or authorized personnel, not entire departments. Without classification, access decisions become arbitrary—and risks increase.
2. Role-Based Access Control (RBAC)
RBAC ensures that employees only have access to the data required to perform their job. Access is assigned based on job roles—engineers get access to dev environments, while finance sees financial systems. This minimizes unnecessary exposure and simplifies access management as roles evolve or people leave the organization.
Real-life scenario: At a mid-sized fintech firm, implementing RBAC reduced help desk requests for access permissions by 40%, while also tightening data access around payroll and compliance systems.
3. Principle of Least Privilege
Access control should follow the principle of least privilege: users are given the minimum level of access required—nothing more. This minimizes risk by ensuring that even if credentials are compromised, the attacker’s scope of damage is limited.
In practice, this means avoiding default 'admin' access or excessive folder permissions granted for convenience. Temporary access should be time-bound and purpose-specific.
4. Access Reviews and Revocation
Granting access is only half the battle—reviewing and revoking access is just as critical. Quarterly or monthly access reviews help ensure permissions are still appropriate.
For example, if a marketing contractor’s access to campaign data is no longer needed, it should be revoked immediately. Without regular audits, orphaned accounts or stale permissions become low-hanging fruit for attackers or insider misuse.
5. Audit Trails and Activity Logging
Strong access control includes visibility into who accessed what, when, and from where. Audit logs provide traceability for incidents and compliance requirements.
Imagine being able to track whether a file containing PII was downloaded after business hours or exported to a personal device—this kind of visibility is essential for proactive threat detection.
Part 4: Why This Matters Now More Than Ever
Access control isn’t a new concept—but its importance has never been greater. As businesses move faster, adopt cloud services, and collect more sensitive data than ever before, the potential for internal data exposure rises exponentially.
Today, data doesn’t live in one place. It’s scattered across cloud storage buckets, SaaS platforms, shared drives, internal dashboards, Slack threads, and production databases. And while security teams work hard to secure perimeters and endpoints, the truth is that many breaches still happen inside the perimeter—often unintentionally.
In Verizon’s 2023 Data Breach Investigations Report, nearly 74% of breaches involved the human element—whether via error, privilege misuse, or compromised credentials.
Cloud-First and AI-Driven = Higher Exposure
With the rise of distributed work and AI-based systems, sensitive data is being copied, transformed, and shared faster than organizations can keep up. Teams spin up data pipelines in minutes. Employees download customer reports for analysis. AI tools access internal documents to train models or generate responses.
Without strong access control, there’s no way to confidently govern:
Who is using what data for what purpose
Whether sensitive data is leaking into dev environments or test sets
If AI outputs are revealing internal documents unintentionally
This growing complexity makes access control not just a security priority—but a business continuity and compliance necessity.
You Can’t Secure What You Can’t See
Visibility is the foundation of security. Without clear access policies and activity logs, teams don’t just risk breaches—they lose control of their own systems.
Consider a healthcare startup that suffered a breach when a non-technical founder used an old credential to access a test database with real patient data—data that was never meant to be exposed outside the clinical team. The issue wasn’t malicious intent. It was a lack of role clarity and access boundaries.
This kind of incident is avoidable with structured access control policies, proper onboarding workflows, and regular access reviews.
Security, Compliance, and Trust Now Start at the Access Layer
Access control sits at the intersection of:
Security: Reduces lateral movement and insider risk
Compliance: Required by every major regulatory framework (GDPR, HIPAA, SOC 2, ISO 27001
Trust: Builds confidence among customers, partners, and regulators
It’s no longer enough to encrypt data and monitor for anomalies. Companies must proactively design for access—starting with data classification, governance policies, and least privilege enforcement.
Access Control is Now Business-Critical Infrastructure
The organizations that thrive in the next decade will be those that build security into the design of their data systems, not bolt it on afterward. That means integrating access controls directly into platform architecture, developer workflows, and operational review processes.
If you're scaling data infrastructure, building with AI, or managing sensitive customer data—access control is no longer a “security feature.” It’s foundational architecture.
Part 5: Final Thoughts & Summary
As businesses grow more data-driven, distributed, and digitally complex, the line between security and usability becomes increasingly thin. It’s not enough to keep data encrypted or monitor for external threats. The real risk often lies in everyday access—who can see what, and whether they should.
Access control is the connective tissue between data governance and data security. It ensures that all the data protections you’ve invested in—encryption, backups, compliance protocols—actually hold up in practice.
When done right, access control is:
A productivity enabler, not a blocker
A governance backbone, not just a checkbox
A business differentiator, not just an IT concern
Organizations that treat it this way will not only avoid breaches and penalties—they’ll build faster, retain trust, and stay ahead of compliance requirements.
You can’t fully govern what you can’t restrict.
You can’t secure what you can’t see.
And you can’t grow what you don’t control.
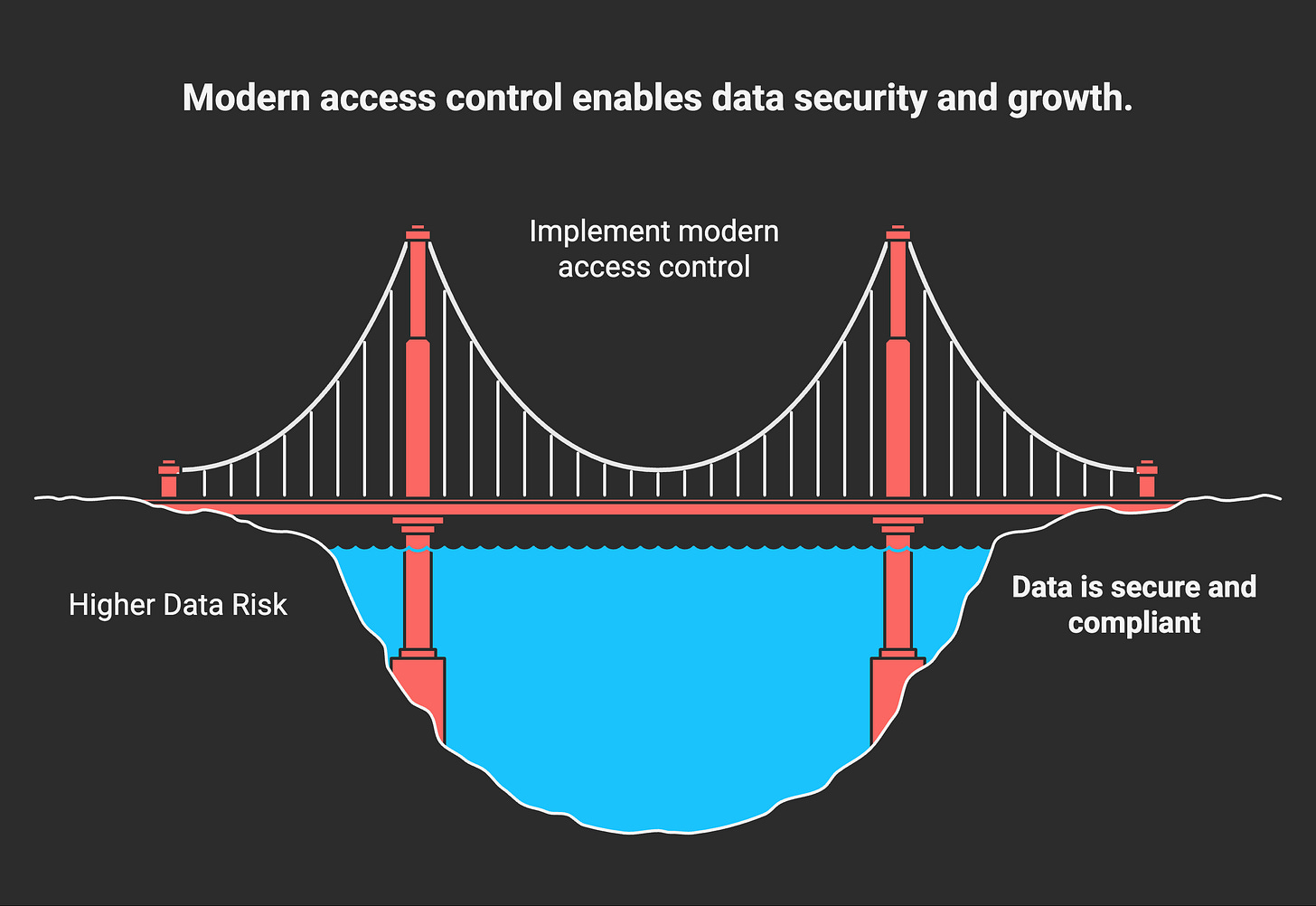
The solution isn’t to lock down everything—but to make access intentional, reviewable, and aligned with business purpose. That’s what modern access control enables. And that’s why it deserves a central place in your data security strategy.
Executive Summary
If you only take five things away from this post:
Access control is foundational to data security—not an add-on.
Most data breaches involve internal access misuse or error.
Strong access policies improve productivity and data quality, not just protection.
Compliance frameworks depend on visible, auditable access control practices.
Modern businesses need to design access control into every system—from day one.
📚 Further Reading & References
The National Institute of Standards and Technology (NIST) Cybersecurity Framework: https://www.nist.gov/cybersecurity-framework
The International Organization for Standardization (ISO) 27001 standard: https://www.iso.org/standard/45170.html
The SANS Institute: https://www.sans.org/
The Data Security and Privacy Protection (DSPP) group of the Institute of Electrical and Electronics Engineers (IEEE): https://www.ieee-security.org/TC/DSPP/
The Center for Internet Security (CIS): https://www.cisecurity.org/